As technology advances, more and more people are becoming aware of the fact that they need to pay more attention to their privacy and how their data is accessed. And that’s where zero knowledge proofs comes in.
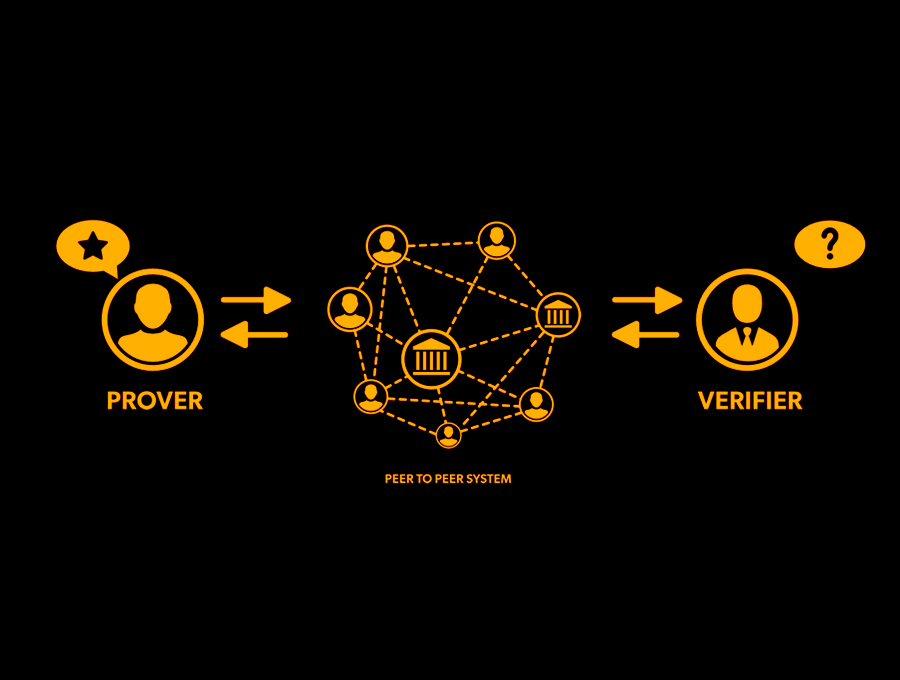
Zero-knowledge proofs (ZKPs) are a cryptographic technique that allows a prover to demonstrate to a verifier that they know some information, without revealing that information. In other words, ZKPs enable a party to prove that they have knowledge of a secret, without revealing any information about the secret itself
Let’s consider 4 of its benefits
Benefits of zero-knowledge proofs
- Privacy: With ZKPs, it is possible to prove the authenticity of information or knowledge without revealing any details about the information itself. This is useful in situations where parties want to protect their privacy and keep sensitive information hidden.
- Security: ZKPs are based on complex mathematical algorithms that make it extremely difficult for an attacker to impersonate a prover or forge a proof. As a result, ZKPs provide strong security guarantees and are useful in a wide range of applications, such as secure authentication and identification.
- Efficiency: ZKPs are designed to be computationally efficient, which means they can be used in real-world applications without significantly slowing down the system. This makes them suitable for use in many different contexts, including online transactions and secure data transfer.
- Trust: ZKPs can be used to build trust between parties who do not know each other or have a history of mistrust. By using ZKPs, parties can verify that the other party has the information or knowledge they claim to have, without needing to trust them directly.
Overall, ZKPs are a powerful tool for enhancing privacy, security, efficiency, and trust in a wide range of applications. They are particularly useful in situations where sensitive information needs to be shared or verified, while maintaining privacy and security.